Recently, Arm released a series of IP to protect the chip from physical attacks. This series extends Arm's secure IP product portfolio and provides physical security for all IoT products. These new IP products are marked with the “P†logo representing physical security, including the Cortex-M35P processor and a new set of security IPs that prevent side-channel attacks (CryptoIsland-300P and CryptoCell-312P). Let us explore together on the weekend leisure time. The main advantages of Cortex-M35P
The Cortex-M35P is the first Armv8-M processor to offer anti-tampering capabilities, making it easier and faster for processor cores to obtain payment-level or carrier-grade security certifications. The Cortex-M35P is an extension of Arm's security portfolio and follows Arm's PSA platform security architecture principles.
| Make your design more confident | Make protection more flexible | Accelerate your product success |
| Provide mature, well-tested and supportive security technologies. | Provide a variety of advanced physical security features for you to choose. | Rich IP products and sound ecosystem support can effectively reduce product development costs. |
| • Built on market proven technology that has been deployed in billions of SecurCore processors. • Get support from billions of Cortex-A-based devices using TrustZone technology. • Reuse existing knowledge on the same programmer model that has been deployed by millions of Cortex-M developers. | • Strengthen market adaptability for the widely familiar Cortex-M series without compromising performance. • Provides high flexibility and optional features for advanced features including signal processing. • Higher security (Lockstep, configurable parity, observability) for faster, lower-cost deployment of system security features. | • Optimize in our comprehensive Arm Security Solutions portfolio. • Easy upgrade from Cortex-M33 processor. • Reuse existing software built on Cortex-M devices. • Supported by the world's first embedded ecosystem, access to the world's largest open knowledge base. |
Why prevent physical attacks?
We encounter more and more devices in our daily lives - such as at home, workplaces, hospitals, industrial sites, urban spaces, and so on - some of which are networked and some are not. Among these, many devices store valuable personal information, making them the targets of physical attacks.
From a cost perspective, these attacks have become more feasible due to the deployment and presence of simple data collection tools. We have witnessed more and more physical attacks, such as side channel attacks have become part of the standard security threat model. The main concern for physical attacks comes from the extended effect of the attack (the resulting harm). That is, by attacking a device, the attacker can extract the source code and discover vulnerabilities, thereby carrying out more extensive network attacks.
Physical attacks related to other types of attacks
As the attack surface continues to grow and the scale of the Internet of Things (IoT) grows exponentially, it may be difficult to determine how to protect your next-generation devices based on the current situation during product design planning. To understand and respond to this situation, Arm describes security by modeling four different types of attack targets: communications, product life cycle, software attacks, and physical attacks, as shown in Figure 2.
The risk to the device depends on the value of the application and the data. Many devices need to consider more attacks that target the underlying system, such as attacks on the underlying software, which can be fully protected by the isolation provided by Arm TrustZone. However, there are other types of user products that need to consider more complex attack risks, such as the risk of various types of physical attacks on the chip.
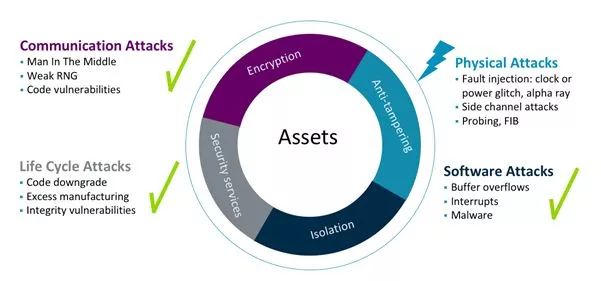
Figure 2: Evaluation of Threat Factors for Four Different Types of Security Attacks
When assessing the equipment and the threats it faces, an important next task is to take appropriate measures to protect your equipment. Arm recommends using a tiered security approach and using the right combination of countermeasures to implement different levels of protection for your equipment.
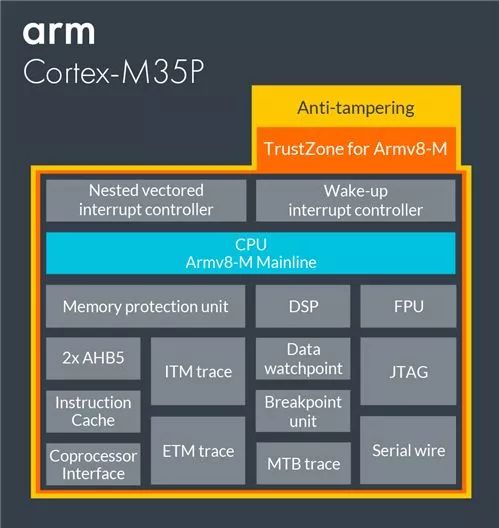
Arm extends a series of IPs to deal with all types of security threats.
Physical protection
When the value of the protected asset is high enough, the hackers have enough incentive to take physical attacks on the device.
2. Instruction cache
Integrated cache improves performance when fetching from embedded Flash.
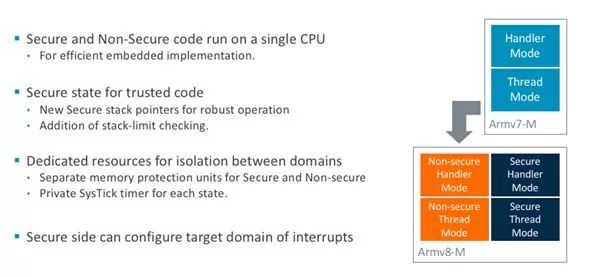
3. TrustZone: The foundation of system-wide security
TrustZone enhances the protection of information security-sensitive functions in the system. It not only provides software isolation of code, memory, and I/O, but also meets real-time, deterministic responses, minimal context switching overhead, and the requirement that the system be easy to software develop.
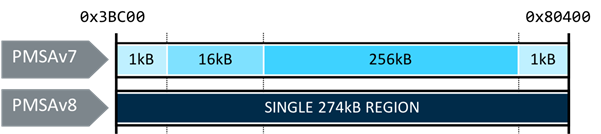
4. Memory Protection Unit (MPU) for Task Isolation
The increase in software reliability and system security can be achieved by limiting each module to only allow access to specific memory areas necessary to complete the function. In this way, the MPU can protect all other memory and peripherals except the resources needed for the current task from corrupted or unauthorized access, significantly improving system reliability.
5. Extensible coprocessor interface
Dedicated computing can be very useful for specific applications. While achieving this expanded computing power, it is equally important to maintain all the advantages of the world’s leading ecosystem—the widest selection of development tools, compilers, debuggers, operating systems, and middleware.
6. Digital Signal Processing (DSP) expansion
In order to accelerate software development, Arm also provides a free DSP library in the CMSIS project. The library contains a series of digital filters, transformations and mathematical functions such as matrices, and supports a range of data types.
to sum up
In summary, physical attacks are one of several potential attacks on embedded or IoT devices. Arm's PSA platform security architecture assesses the level of security that designers need to pass through the threat modeling process in order to employ appropriate countermeasure combinations. Physical attacks are becoming simpler and cheaper, so advanced chip protection technology is crucial. However, physical security design is usually more complicated.
Pu Leather Phone Case,Pu Leather Iphone Case,Best Pu Leather Phone Case,Pu Leather Phone Case For Sale
Guangzhou Jiaqi International Trade Co., Ltd , https://www.make-case.com