Abstract: For military equipment, especially portable military equipment (such as radio stations), the physical security of the key is critical. The use of specially designed components can meet the standard requirements of practical applications and can provide additional protection measures. These components provide protection for the generation and storage of digital keys on electrical and physical structures.
This article was also published in Maxim Engineering Journal, Issue 62 (PDF, 1.1MB).
The essence of confidential communication is to protect the key. To a certain extent, a longer key can prevent the code from being cracked by tough computing techniques, but such protection measures cannot meet the same important physical security requirements. In order to fundamentally solve the problem of physical security, several issues must be considered, including: the physical mechanism for generating random keys, preventing secretly electronic interception when keys are transferred between authentication agents, and preventing physical and mechanical reconnaissance from being secretly Tested security key storage method.
Maxim's DS36xx series of safety monitors adopt a series of unique functions from package design to external sensor interface to internal circuit architecture, providing military electronics design engineers with all the functions they need. After the device has these characteristics, it is easier to meet the requirements of traditional and emerging portable military computing and communication safety standards. Therefore, these devices have strong application potential, as shown in Figure 1.
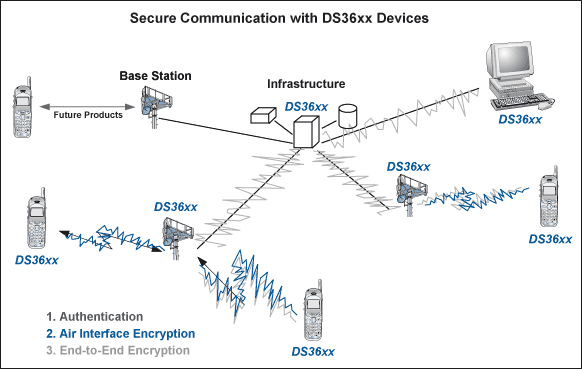
Figure 1. DS36xx devices are suitable for a variety of current and future military and national secret communications functions, including secure communications and customer authentication
Electronic data security requirements In the Federal Information Processing Standard (FIPS), the US government stipulates that cryptographic modules must meet strict (not yet graded) application requirements. This standard is published by the National Institute of Standards and Technology (NIST). The FIPS 140-2 standard has four basic levels: Level 1: Security Level: No physical security mechanism required (only NIST standardized cryptographic algorithms are implemented) Level 2: Security Level Trace physical security Level 3: Tamper-proof physical security Level 4: Physical security provides a protective layer For military communications applications that require a high level of security, the design must comply with the National Security Agency (NSA) Type 1 certification standard. NSA certified devices are used to encrypt confidential US government information. The certification process is very strict, including the testing and analysis of the following items: Password security function security tamper-proof launch security product production and distribution security must meet these standards. A common device is to work in the combat information network tactics (WIN-T) system Communication equipment, this tactical communication protocol is used on the front lines of war. WIN-T supports multiple data, voice and video functions. The network provides reliable mobile broadband communication support, enabling soldiers to maintain a smooth connection at all times. WIN-T uses common communication technologies such as wireless local area network (WLAN), voice over Ethernet protocol (VoIP), and third-generation cellular / satellite communication technologies. WIN-T connects communications between soldiers in combat ground areas and commanders of the Department of Defense (DoD) Global Network.
Any military equipment, WIN-T information security is very important. The architecture of WIN-T must allow authenticated users to freely access the network, while also being able to monitor and reject illegal attacks. Similarly, the WIN-T security function must be built in from the beginning, rather than adding security protection afterwards. This method ensures the safe and confidential transmission of voice and data on the network.
In the past, the main goal of system design was rapid deployment, while security functions were implemented through field updates. The main reason for this approach is that people often think that the built-in security features are very expensive and may delay the plan. However, current military communications equipment requires advanced security features from the beginning, improving versatility and connectivity, and meeting the requirements of FIPS 140-2, NSA, and WIN-T. In other military applications, security and intrusion prevention have gradually become key factors. For example, General Dynamics® and Secure CompuTIng® recently developed by MESHnet Firewall have been used in combat vehicles.
In summary, if a new generation of military communication systems or components cannot first meet the application standards, they cannot be put into use. In particular, military communications equipment is currently required to meet at least FIPS 140-2 security levels 3 and 4. Moreover, in more advanced applications, design engineers must also comply with NSA Class 1 and the newly implemented WIN-T specifications. Normally, military applications require at least FIPS 140-2 safety level 3 certification.
Meeting security requirements is a difficult task for system designers to meet the security requirements issued by the US government. As the factors that pose a potential threat to the system continue to increase, the security standards also change, and the security requirements become more demanding over time.
In order to keep up with changes in safety standards, designers need to solve many difficult problems, because the design process must consider the requirements of the safety level, and the ultimate purpose of the designed safety equipment. For example, only re-encrypting the key will not significantly improve the security of the key, because there are already mature technologies that can steal the key. Therefore, several different methods need to be used in combination to ensure the security of the key, including enhanced physical security.
When designing a secure military system that meets the requirements of FIPS 140-2 (3rd and 4th security level), NSA Class 1 or WIN-T, it is important to use devices with comprehensive tamper-proof technology. Can be effective. Maxim's DS36xx series products, such as the DS3600 shown in Figure 2, can actively detect tampering intrusion even when the battery is powered, providing an integrated solution to ensure the security of keys and critical data (when the main power fails, it will respond immediately to ensure Smooth work). Regardless of whether there is a power supply, the on-chip power monitor and battery switch ensure that all tampering monitoring mechanisms always maintain effective work. The device continuously detects the main power supply—when it drops to the lower threshold, it automatically switches to the external backup battery immediately to keep the internal and external protection circuits working. In this way, tamper detection is not interrupted when the main power supply of the device fails.
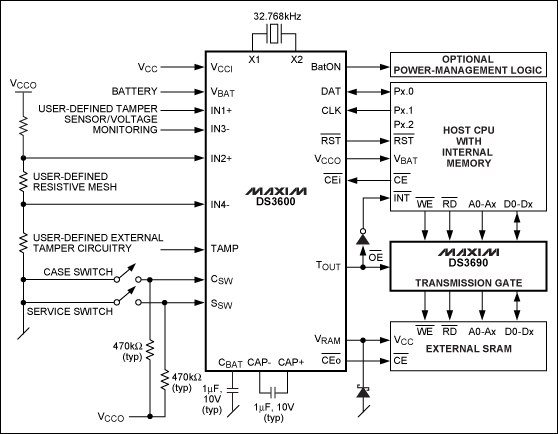
Figure 2. The DS3600 security monitor uses both monitoring functions and security mechanisms to detect tampering and protect the contents of battery-backed volatile memory, such as internally stored keys and other sensitive data stored in external SRAM
In order to meet the requirements of FIPS 140-2 (3rd and 4th security level) and NSA Class 1 and WIN-T specifications, tamper detection devices should allow designers to add their own external sensors so that they can be protected in storage The data device provides a protective layer around the device, that is, the security boundary. By attaching external sensors to the DS36xx series, system designers have a unique and flexible method to join the application security layer, thus meeting the various standard requirements issued by government departments.
To meet the requirements of various government standards, the DS36xx safety monitor can simultaneously monitor the analog supply voltage, digital signals, and resistive network protection sensor grids. In addition, all DS36xx devices are available in chip-scale ball grid array (CSBGA) packages (see Figure 3). By strictly restricting access to mounted device pins, these packages also provide another layer of passive physical security protection for control protection and data signals.

Figure 3. After the device is mounted on the circuit board, the DS36xx series of CSBGA packages restrict access to I / O signals, thus providing a passive protective layer
Internal security DS36xx devices also include other layers of protection to implement internal tamper detection mechanisms. These internal detection mechanisms improve the interface capability of the device and the custom configuration of external tamper detection sensors. The internal tamper detection mechanism includes an on-chip temperature sensor, unpacking monitor, power monitor, battery monitor, and oscillator monitor to provide continuous tamper detection. The monitoring function always works, especially when using battery power.
For external security mechanisms, when a user-defined or factory-set threshold is reached, the internal protection mechanism is triggered. For example, to meet the required certification bodies such as NSA, as well as FIPS and WIN-T standards, designers can use an internal temperature sensor to monitor the substrate temperature. Once the upper and lower temperature thresholds are reached, the device initiates an anti-tamper response.
In addition to measuring instantaneous temperature, DS36xx also provides other temperature detection functions. In particular, the rate change detector monitors the rate of substrate temperature change. The rapid increase or decrease of temperature will trigger the device's anti-tamper response, providing additional protection against the intrusion of higher-level encrypted data recovery technology.
One way to recover data from protected SRAM is to add liquid nitrogen before the device is powered off. This method extends the retention time of SRAM data without power to the millisecond level. However, the temperature monitoring function of the DS36xx series can determine this tampering event. Before the low-temperature memory retention function takes effect, the device will erase its internal memory. The memory is connected by hardware, and the high-speed erase function can clear the entire storage array in less than 100ns. Other tampering events (for example, the bottom of the interlock) or sending commands directly to the I²C / SPI ™ compatible interface of the device can also trigger this function.
The DS36xx devices also have a proprietary technology—non-marking key storage †. The imprint-free key memory solves the security problem caused by the accumulation or depletion of the oxide layer of the SRAM memory cell (depending on the stored data). The long-term storage of data in this type of traditional storage unit changes with time to produce oxide layer strain, leaving data memory in the storage location. Even after clearing these units, the data can be read out.
The newly developed non-memory key storage technology avoids oxidative strain. This technology improves the device's ordinary battery-powered SRAM memory. Therefore, when a tampering event is detected or the memory is directly cleared by command, the entire memory is cleared, leaving no trace of data that might be recovered. Application product designers in military and government agencies can use this feature to develop unique and very secure products that store highly sensitive keys.
Tampering Event Response DS36xx devices continuously monitor all the above tampering intrusion events. After tampering is detected, an anti-tampering response is made immediately through an internal or external anti-tampering mechanism. Detecting tampering events starts with identifying the source of the tampering, and the tampering event will be locked until the state that caused the tampering event is cleared. Only then will the tampering event be reset. Table 1 lists the steps taken by DS36xx devices during the tamper response.
Table 1. Steps to be taken when DS36xx devices detect tampering events
Supporting highly secure military applications requires not only physical security measures to protect stored keys, but physical key generation also requires physical security. That is, the method used to generate the digital key must ensure that the key is not copied illegally, whether it is the same device (which violates the purpose of the DS36xx series of secure data storage), or a complete copy of the device.
The Random Number Generator (RNG) of the DS36xx devices uses a deterministic pseudo-random algorithm and uses two random sources that come with the chip to generate seeds. This function provides a continuous bit stream, which is processed by the host CPU to form the seed of the authentication software RNG function. Moreover, each DS36xx safety monitor contains a unique chip serial number preset at the factory, which can be read through the I / O port. The chip serial number provides users with a unique way to identify each final product.
In addition, the latest DS36xx devices can also erase certain special memory cells based on the type of tampering. This function is called the erase level (see Table 2 Devices) and is suitable for applications where the entire device maintains integrity. That is, after tampering, although not all functions can be used, it can continue to use the device to a certain extent. Communication equipment belongs to such applications, such as security military communication equipment. Even if there is a tampering event, the equipment must have certain working capabilities.
Table 2. DS36xx devices and their unique features
In addition to advanced data security features, many defense applications also require a wide operating and storage temperature range. Although DS36xx devices are mainly used to provide higher safety functions in ordinary working environments, some of the latest products in this series also support a wider operating temperature range to reach the entire military-grade temperature range (DS36xx is -55 ° C to + 95 ° C, while the military grade range is -55 ° C to + 125 ° C).
This article was also published in Maxim Engineering Journal, Issue 62 (PDF, 1.1MB).
The essence of confidential communication is to protect the key. To a certain extent, a longer key can prevent the code from being cracked by tough computing techniques, but such protection measures cannot meet the same important physical security requirements. In order to fundamentally solve the problem of physical security, several issues must be considered, including: the physical mechanism for generating random keys, preventing secretly electronic interception when keys are transferred between authentication agents, and preventing physical and mechanical reconnaissance from being secretly Tested security key storage method.
Maxim's DS36xx series of safety monitors adopt a series of unique functions from package design to external sensor interface to internal circuit architecture, providing military electronics design engineers with all the functions they need. After the device has these characteristics, it is easier to meet the requirements of traditional and emerging portable military computing and communication safety standards. Therefore, these devices have strong application potential, as shown in Figure 1.

Figure 1. DS36xx devices are suitable for a variety of current and future military and national secret communications functions, including secure communications and customer authentication
Electronic data security requirements In the Federal Information Processing Standard (FIPS), the US government stipulates that cryptographic modules must meet strict (not yet graded) application requirements. This standard is published by the National Institute of Standards and Technology (NIST). The FIPS 140-2 standard has four basic levels: Level 1: Security Level: No physical security mechanism required (only NIST standardized cryptographic algorithms are implemented) Level 2: Security Level Trace physical security Level 3: Tamper-proof physical security Level 4: Physical security provides a protective layer For military communications applications that require a high level of security, the design must comply with the National Security Agency (NSA) Type 1 certification standard. NSA certified devices are used to encrypt confidential US government information. The certification process is very strict, including the testing and analysis of the following items: Password security function security tamper-proof launch security product production and distribution security must meet these standards. A common device is to work in the combat information network tactics (WIN-T) system Communication equipment, this tactical communication protocol is used on the front lines of war. WIN-T supports multiple data, voice and video functions. The network provides reliable mobile broadband communication support, enabling soldiers to maintain a smooth connection at all times. WIN-T uses common communication technologies such as wireless local area network (WLAN), voice over Ethernet protocol (VoIP), and third-generation cellular / satellite communication technologies. WIN-T connects communications between soldiers in combat ground areas and commanders of the Department of Defense (DoD) Global Network.
Any military equipment, WIN-T information security is very important. The architecture of WIN-T must allow authenticated users to freely access the network, while also being able to monitor and reject illegal attacks. Similarly, the WIN-T security function must be built in from the beginning, rather than adding security protection afterwards. This method ensures the safe and confidential transmission of voice and data on the network.
In the past, the main goal of system design was rapid deployment, while security functions were implemented through field updates. The main reason for this approach is that people often think that the built-in security features are very expensive and may delay the plan. However, current military communications equipment requires advanced security features from the beginning, improving versatility and connectivity, and meeting the requirements of FIPS 140-2, NSA, and WIN-T. In other military applications, security and intrusion prevention have gradually become key factors. For example, General Dynamics® and Secure CompuTIng® recently developed by MESHnet Firewall have been used in combat vehicles.
In summary, if a new generation of military communication systems or components cannot first meet the application standards, they cannot be put into use. In particular, military communications equipment is currently required to meet at least FIPS 140-2 security levels 3 and 4. Moreover, in more advanced applications, design engineers must also comply with NSA Class 1 and the newly implemented WIN-T specifications. Normally, military applications require at least FIPS 140-2 safety level 3 certification.
Meeting security requirements is a difficult task for system designers to meet the security requirements issued by the US government. As the factors that pose a potential threat to the system continue to increase, the security standards also change, and the security requirements become more demanding over time.
In order to keep up with changes in safety standards, designers need to solve many difficult problems, because the design process must consider the requirements of the safety level, and the ultimate purpose of the designed safety equipment. For example, only re-encrypting the key will not significantly improve the security of the key, because there are already mature technologies that can steal the key. Therefore, several different methods need to be used in combination to ensure the security of the key, including enhanced physical security.
When designing a secure military system that meets the requirements of FIPS 140-2 (3rd and 4th security level), NSA Class 1 or WIN-T, it is important to use devices with comprehensive tamper-proof technology. Can be effective. Maxim's DS36xx series products, such as the DS3600 shown in Figure 2, can actively detect tampering intrusion even when the battery is powered, providing an integrated solution to ensure the security of keys and critical data (when the main power fails, it will respond immediately to ensure Smooth work). Regardless of whether there is a power supply, the on-chip power monitor and battery switch ensure that all tampering monitoring mechanisms always maintain effective work. The device continuously detects the main power supply—when it drops to the lower threshold, it automatically switches to the external backup battery immediately to keep the internal and external protection circuits working. In this way, tamper detection is not interrupted when the main power supply of the device fails.

Figure 2. The DS3600 security monitor uses both monitoring functions and security mechanisms to detect tampering and protect the contents of battery-backed volatile memory, such as internally stored keys and other sensitive data stored in external SRAM
In order to meet the requirements of FIPS 140-2 (3rd and 4th security level) and NSA Class 1 and WIN-T specifications, tamper detection devices should allow designers to add their own external sensors so that they can be protected in storage The data device provides a protective layer around the device, that is, the security boundary. By attaching external sensors to the DS36xx series, system designers have a unique and flexible method to join the application security layer, thus meeting the various standard requirements issued by government departments.
To meet the requirements of various government standards, the DS36xx safety monitor can simultaneously monitor the analog supply voltage, digital signals, and resistive network protection sensor grids. In addition, all DS36xx devices are available in chip-scale ball grid array (CSBGA) packages (see Figure 3). By strictly restricting access to mounted device pins, these packages also provide another layer of passive physical security protection for control protection and data signals.

Figure 3. After the device is mounted on the circuit board, the DS36xx series of CSBGA packages restrict access to I / O signals, thus providing a passive protective layer
Internal security DS36xx devices also include other layers of protection to implement internal tamper detection mechanisms. These internal detection mechanisms improve the interface capability of the device and the custom configuration of external tamper detection sensors. The internal tamper detection mechanism includes an on-chip temperature sensor, unpacking monitor, power monitor, battery monitor, and oscillator monitor to provide continuous tamper detection. The monitoring function always works, especially when using battery power.
For external security mechanisms, when a user-defined or factory-set threshold is reached, the internal protection mechanism is triggered. For example, to meet the required certification bodies such as NSA, as well as FIPS and WIN-T standards, designers can use an internal temperature sensor to monitor the substrate temperature. Once the upper and lower temperature thresholds are reached, the device initiates an anti-tamper response.
In addition to measuring instantaneous temperature, DS36xx also provides other temperature detection functions. In particular, the rate change detector monitors the rate of substrate temperature change. The rapid increase or decrease of temperature will trigger the device's anti-tamper response, providing additional protection against the intrusion of higher-level encrypted data recovery technology.
One way to recover data from protected SRAM is to add liquid nitrogen before the device is powered off. This method extends the retention time of SRAM data without power to the millisecond level. However, the temperature monitoring function of the DS36xx series can determine this tampering event. Before the low-temperature memory retention function takes effect, the device will erase its internal memory. The memory is connected by hardware, and the high-speed erase function can clear the entire storage array in less than 100ns. Other tampering events (for example, the bottom of the interlock) or sending commands directly to the I²C / SPI ™ compatible interface of the device can also trigger this function.
The DS36xx devices also have a proprietary technology—non-marking key storage †. The imprint-free key memory solves the security problem caused by the accumulation or depletion of the oxide layer of the SRAM memory cell (depending on the stored data). The long-term storage of data in this type of traditional storage unit changes with time to produce oxide layer strain, leaving data memory in the storage location. Even after clearing these units, the data can be read out.
The newly developed non-memory key storage technology avoids oxidative strain. This technology improves the device's ordinary battery-powered SRAM memory. Therefore, when a tampering event is detected or the memory is directly cleared by command, the entire memory is cleared, leaving no trace of data that might be recovered. Application product designers in military and government agencies can use this feature to develop unique and very secure products that store highly sensitive keys.
Tampering Event Response DS36xx devices continuously monitor all the above tampering intrusion events. After tampering is detected, an anti-tampering response is made immediately through an internal or external anti-tampering mechanism. Detecting tampering events starts with identifying the source of the tampering, and the tampering event will be locked until the state that caused the tampering event is cleared. Only then will the tampering event be reset. Table 1 lists the steps taken by DS36xx devices during the tamper response.
Table 1. Steps to be taken when DS36xx devices detect tampering events
| Step | AcTIon |
| 1 | The internal encrypTIon key is immediately, completely, and acTIvely erased (if applicable). |
| 2 | The external RAM is erased (if applicable). |
| 3 | The tamper-latch registers record the state of the tamper input sources. |
| 4 | The tamper output asserts to alert the system processor. |
| 5 | The tamper-event time-stamp register records the time of the tamper event. |
Supporting highly secure military applications requires not only physical security measures to protect stored keys, but physical key generation also requires physical security. That is, the method used to generate the digital key must ensure that the key is not copied illegally, whether it is the same device (which violates the purpose of the DS36xx series of secure data storage), or a complete copy of the device.
The Random Number Generator (RNG) of the DS36xx devices uses a deterministic pseudo-random algorithm and uses two random sources that come with the chip to generate seeds. This function provides a continuous bit stream, which is processed by the host CPU to form the seed of the authentication software RNG function. Moreover, each DS36xx safety monitor contains a unique chip serial number preset at the factory, which can be read through the I / O port. The chip serial number provides users with a unique way to identify each final product.
In addition, the latest DS36xx devices can also erase certain special memory cells based on the type of tampering. This function is called the erase level (see Table 2 Devices) and is suitable for applications where the entire device maintains integrity. That is, after tampering, although not all functions can be used, it can continue to use the device to a certain extent. Communication equipment belongs to such applications, such as security military communication equipment. Even if there is a tampering event, the equipment must have certain working capabilities.
Table 2. DS36xx devices and their unique features
| Part | I / O | No. of Analog Voltages Monitored | No. of Digital Inputs Monitored | Operating Temperature Range (° C) | Internal Key Memory (Bytes) | External Memory Control | Random Number Generator | Overvoltage Monitor | Battery Monitor | Erasure Hierarchy |
| DS3600 | 3-wire | 4 | 1 | -40 to +85 | 64 | √ | √ | √ | ||
| DS3605 | I²C | 4 | 1 | -40 to +85 | N / A | √ | √ | √ | ||
| DS3640 | I²C | 5 | 3 | -40 to +85 | 1k | √ | √ | √ | ||
| DS3641 | 4-wire | 5 | 3 | -40 to +85 | 1k | √ | √ | √ | ||
| DS3644 * | I²C | 12 | 4 | -55 to +95 | 1k | √ | √ | √ | √ | 2 levels |
| DS3645 * | I²C | 12 | 4 | -55 to +95 | 4k | √ | √ | √ | √ | |
| DS3650 | 4-wire | 2 | N / A | -40 to +85 | N / A | √ | √ | |||
| DS3655 * | I²C | N / A | 4 | -40 to +85 | 64 | |||||
| DS3665 * | SPI | 12 | 4 | -55 to +95 | 8k | √ | √ | √ | √ | 4 levels |
In addition to advanced data security features, many defense applications also require a wide operating and storage temperature range. Although DS36xx devices are mainly used to provide higher safety functions in ordinary working environments, some of the latest products in this series also support a wider operating temperature range to reach the entire military-grade temperature range (DS36xx is -55 ° C to + 95 ° C, while the military grade range is -55 ° C to + 125 ° C).

A solar cell panel, solar electric panel, photo-voltaic (PV) module, PV panel or Solar Panel is an assembly of photovoltaic solar cells mounted in a (usually rectangular) frame, and a neatly organised collection of PV panels is called a photovoltaic system or solar array. Solar panels capture sunlight as a source of radiant energy, which is converted into electric energy in the form of direct current (DC) electricity.
60w Solar Panel,Solar Panel System For Home,Solar Panels 200 Watt,Solar Panels
suzhou whaylan new energy technology co., ltd , https://www.whaylanenergy.com