The advancement of microelectronics technology, computing technology and wireless communication technology has promoted the rapid development of low-power multifunction sensors, enabling them to integrate multiple functions such as information collection, data processing and wireless communication in a small volume. The sensor network is a multi-hop self-organizing network system formed by a large number of inexpensive mini-sensor nodes deployed in the detection area through wireless communication. Its purpose is to cooperatively sense, collect and process the objects in the network coverage area Message and send it to the observer. Sensors, perception objects and observers constitute the three elements of the sensor network.
In most non-commercial applications, such as environmental monitoring, forest fire prevention, migratory bird migration tracking and other applications, safety issues are not a very important issue. In other areas where strict confidentiality measures are required, such as commercial cell wireless security networks and military surveillance of enemy-deployed sensor networks in enemy-controlled areas, the security of sensor networks is very important.
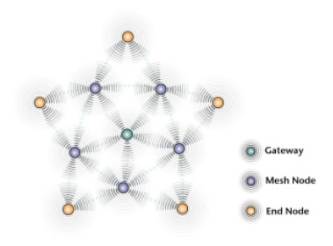
1 Sensor network security solution
Sensor networks have many distinctive features, such as limited communication capabilities, limited power supply energy, limited computing power and storage space, dense sensor node configuration, and flexible network topology. These characteristics pose a series of challenges for the design of security solutions [2 ]. A relatively complete sensor network solution should have the following basic characteristics: confidentiality, authenticity, integrity, freshness, scalability, availability, self-organization, and robustness.
The security issues currently studied are divided into three layers, which can be divided into the following order from top to bottom:
(1) Safe routing. From the perspective of maintaining route security, look for routes as safe as possible to ensure network security;
(2) Key management. Consider the communication security between two nodes, starting from the perspective of how to generate a secure key, how to distribute the key, how to exchange the key, and how to authenticate;
(3) Key algorithm. Start from an algorithm perspective.
2 Security and performance evaluation of sensor network key management
The characteristics of the sensor network and the existing resource limitations make the sensor network more difficult to resist various attacks than the traditional network. The key management scheme of the sensor network needs to have the following characteristics:
(1) Security. The security of key management is the primary consideration, including confidentiality, integrity, availability, etc.
(2) Invulnerability. An ideal key management scheme should be that after some nodes are attacked, the impact on secure communication between other normal nodes is almost zero.
(3) Scalability. The scale of WSN nodes ranges from a dozen to as many as tens of thousands. With the expansion of the scale, the calculation, storage and communication overhead required for key negotiation will increase, and the key management scheme and protocol must be able to adapt to different sizes of WSN.
(4) Effectiveness. The situation where the storage, processing and communication capabilities of network nodes are very limited must be fully considered.
(5) Key connectivity. The probability of directly establishing a communication key between nodes. Maintaining a sufficiently high key connection probability is a necessary condition for WSN to perform its due function.
(6) Dynamic changes of the network. The scheme should support the expansion of the network, and can guarantee the forward security of the network, that is, the new node cannot obtain the secret information transmitted in the network before it joins.
(7) Certification. Through the authentication between nodes, you can resist multiple attacks, such as copy nodes, fake nodes and other attack methods. Therefore, whether the authentication between nodes can be achieved is also an important evaluation index of the key management scheme of the sensor network.
All-in-one Energy Storage System
An energy storage system (ESS) is a device or set of devices used to store energy for later use. ESSs can store energy in various forms, including chemical, mechanical, thermal, and electrical energy. The stored energy can be used to power homes, buildings, or vehicles, or to supplement the power grid during periods of high demand.

ESSs are becoming increasingly important as renewable energy sources such as solar and wind power become more popular. These sources of energy are intermittent, meaning they only produce electricity when the sun is shining or the wind is blowing. ESSs can help to smooth out these fluctuations in energy production and make renewable energy more reliable and cost-effective.

ESS is an integrated battery system that stores your solar energy for backup protection, so when the grid goes down your power stays on. Your system detects outages and automatically recharges with sunlight to keep your appliances running for days.GOOTU offers a modular, flexible design and can be easily customized to meet diverse customer needs.
Energy Storage System,Home Energy Storage System, Modular LiFePO4 Battery,Solar Energy Storage System,Renewable Energy Storage System
Shenzhen Jiesai Electric Co.,Ltd , https://www.gootuenergy.com