On April 23, 2018, BEC (US chain) broke the ERC20 protocol security vulnerability. The attacker used the integer overflow BUG to generate tokens indefinitely, which directly caused the BEC currency to dive, almost zero.
On the evening of May 2, Mito Cai Wensheng answered many questions about BEC again during the interaction of WeChat Group.
Cai Wensheng emphasized: "BEC's beauty chain is not made by Meitu, nor is it personally made by me." But netizens don't seem to buy it.
As a low-level platform for value circulation, security is the top priority of the blockchain, and it is also one of the cornerstones that the blockchain can be widely accepted by society. How to reduce the occurrence of risk events through good vulnerability management ecology will become more important.
Looking back at the development of the blockchain for nine years, the huge financial losses caused by security incidents and the bankruptcy of the company are numerous.
Let us first analyze the current situation of the three major types of security incidents such as Bitcoin, Ethereum and Exchange, and then discuss how to comprehensively build the blockchain security ecosystem from the three aspects of project team, project ecology and investor prevention. Effectively reduce security risks.
Status of security issues
1. Bitcoin security issuesSince the Bitcoin blockchain has been running since January 4, 2009, it has been running steadily for 3,405 days, and its security is impregnable.
However, with the development of encryption technology, Bitcoin security mechanisms are increasingly challenged.
An organization of cryptographic algorithm enthusiasts (Large Bitcoin Collider (LBC)) is working on a Don Quixote-style effort:
Violently crack the encryption algorithm that creates the bitcoin wallet address.
LBC has been online for less than a year, and the project side said they have generated 3,000 trillion keys and compared them to existing bitcoin wallet addresses. At present, a total of 30 matching keys have been selected, and the "fishing" key has been removed. There are already 3 matching keys that actually contain bitcoin.
In addition to the brute force law, Bitcoin's biggest security risk comes from the fact that the exchange platform is hacked or hacked, or the user's account is stolen.
Once stolen, the hacker will wash the white through the means of mixing coins, and the possibility of recovery is almost zero.
2. Ethereum safety issuesCompared to Bitcoin, Ethereum's biggest improvement is the introduction of smart contracts on the one hand.
On the one hand, its Turing-complete programming mechanism enables the platform to support complex applications, greatly enriching the diversity of platform applications;
On the other hand, Ethereum introduced the middle layer of the virtual machine, enabling smart contracts developed in multiple languages ​​to run on the platform and improve the scalability of the platform.
But it is precisely these two mechanisms that add more uncertainty to the safety of Ethereum.
First of all, Turing's complete programming approach is more flexible, but at the same time more complex and uncontrollable;
Second, the virtual machine mechanism allows Ethereum to support multiple languages, and of course introduces more language uncertainty, complexity, and inherent flaws.
These factors are all hotbeds for hackers looking for prey.
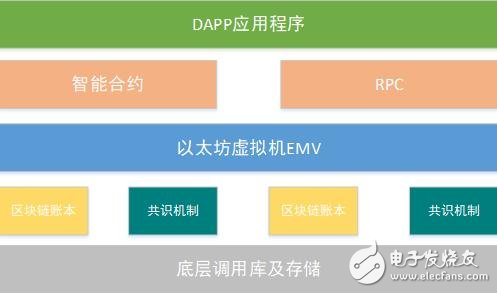
Ethereum architecture diagram
As the most active public-chain platform in the blockchain, Ethereum, there are known vulnerabilities such as Solidity vulnerability, short address vulnerability, transaction order dependency, timestamp dependency, and reentrant attack.
Vulnerabilities may be exploited when the contract is invoked, and features that are difficult to update after the smart contract is deployed also make the impact of the vulnerability more widespread and durable.
Some research institutions use analysis tools Maian to analyze nearly one million smart contracts based on Ethereum, and found that 34,200 contracts contain security holes that can steal or freeze assets or even delete contracts.
3. Exchange security issues
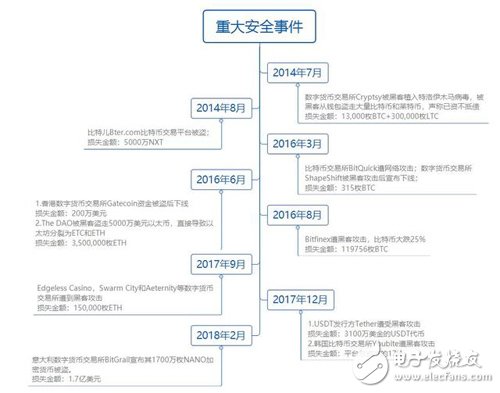
As a huge pool of digital assets, the exchange has become an important target for hackers to attack. If the security control is not in place, any attack will be a heavy loss, and bankruptcy will only be overnight.
In addition to attacks from outside, it is very deadly and terrible to smuggle or leak information from inside the exchange. In April 2018, Coinsecure, an Indian-based exchange, announced that 438.318 bitcoins worth $3.3 million were stolen, allegedly because of an employee.
According to foreign media Cointelegraph, the Korean media website MBC hired a security company to test the security settings of five Korean bitcoin exchanges including Bithumb, and the results were worrying.
Security companies have used some of the so-called basic hacking tools to successfully circumvent the security procedures of these bitcoin exchanges. The company said they can successfully invade all five target platforms to obtain user data and funds.
Building blockchain security ecologyBlockchain security ecology not only requires project teams, developers, but also multi-party cooperation. Therefore, this paper mainly discusses the safety of blockchain from the three aspects of project team internal control, project ecological incentives and investor self-prevention. Construction.
Improve the code security review mechanismLooking back at the ERC20 vulnerability incident, it is known that the destruction of BEC is just an integer overflow vulnerability. Students who have studied computers may know that such vulnerabilities are the most common and common vulnerabilities in the program, and can be avoided through effective code security review mechanisms. .
After the loophole incident, after verification, there are more than 20 projects using the ERC20 protocol, and the quality of the code is very worrying!
The ever-changing currency circle is really developing too fast. Everyone is flying forward. They are rushing to write white papers, rushing to raise funds, and rushing to the project. Naturally, few people sink their minds to do the test and do it well. Security review has led to frequent loopholes and frequent security incidents.
Blockchain is a distributed decentralized system. Once the code is deployed, it will be difficult to update. The code needs to be upgraded by hard fork or soft fork. The cost is not high.
The THE DAO event directly splits Ethereum into ETH and ETC, which is a major disruption to the Ethereum ecology. So before the project was released, adequate testing and code review became critical and necessary. For example, multi-person code review, internal evaluation team, external expert evaluation, etc.
Multi-person code reviewSince one's ability and cognition are always limited, different people will find different problems for the same piece of code. The multi-person code review mechanism can greatly reduce the BUG rate and vulnerability rate of the code. This approach is also one of the most versatile and effective ways for the software industry to reduce error rates.
Internal assessment teamThe project team established an internal safety assessment team to sort out the list of common safety issues in the industry, and conduct safety audits on a project-by-pair basis. Through simple combing and evaluation, common basic vulnerabilities can be swept away, greatly increasing the reliability of the system. Sex.
External expert evaluationFor some new and specific vulnerabilities, the project team can sort out and evaluate with the help of external security experts, and strive to minimize security risks before the project is released.
Develop white hat hacking incentivesThe world is nothing more than two poles, one yin and one yang, one black and one white, one right and one evil. There are hackers who want to destroy it, and there are white hat hackers to maintain world justice.
As the market value of various types of digital assets is getting higher and higher, the benefits that hackers take from them are becoming more and more objective. By contrast, white-hat hackers are much more sour. This huge income gap has led to more and more people joining the hacker camp, while white hat hackers are rare.
By motivating white hat hackers to suppress or balance hackers' increasingly unscrupulous sabotage behavior may become an effective means.
So how do you motivate white hat hackers to contribute to the platform?
Mainly can start from two aspects, one is material incentives, and the other is spiritual incentives.
Material incentiveFor the public chain that issues the certificate, the most substantial material incentive is naturally the certificate. It is not only the value carrier of the blockchain platform, but also an important means of platform ecological governance. For example, COSMOS, in order to encourage discovery and timely report defects, Cosmos Hub allows hackers to "invite" through ReportHackTx transactions, mainly to explain, "This node has been attacked, please award the award to this address." A hacker can receive 5% of the hit asset as a bounty.
In addition, we can also encourage white hat hackers to actively exploit vulnerabilities by setting up hacker bonus pools, hacker funds or project special consultants to help the platform run for a long time and safely.
Mental stimulationIn addition to material rewards, for Hacker, a very different and charismatic group, spiritual motivation may be a more lasting and effective way. For each hacker who contributes to the platform or project, the project team, foundation, or community should be rewarded with the appropriate honors. It can be a leaderboard, a contribution value, or a scarce title, etc., so that it can be not only known to other members of the community, but also significantly different from ordinary members, enhancing its sense of presence, participation and honor in the community.
Choose a reliable exchangeThere are two reasons why exchanges have become the hardest hit areas of security incidents:
On the one hand, it is because the exchange stores the huge digital assets of investors;
On the other hand, the blockchain industry is developing rapidly. The security construction of the centralized exchanges cannot keep up with the development speed of its business. In particular, the exchanges of various types of exchanges are uneven, the security issues are very prominent, and the interests of investors are difficult to be guaranteed.
To this end, decentralized exchanges are hot, but because of the difficulty in improving their trading efficiency, the technology is difficult to implement, and it is not yet possible to completely replace the centralized exchange.
Therefore, from the perspective of protecting the interests of the people, it is very important for investors to choose to run a long-term, reliable and secure trading platform.
Car Radio Antenna.car satellite TV Antenna.High gain car radio antenna
car radio antenna,car satellite tv antenna,High gain car radio antenna
Yetnorson Antenna Co., Ltd. , https://www.yetnorson.com